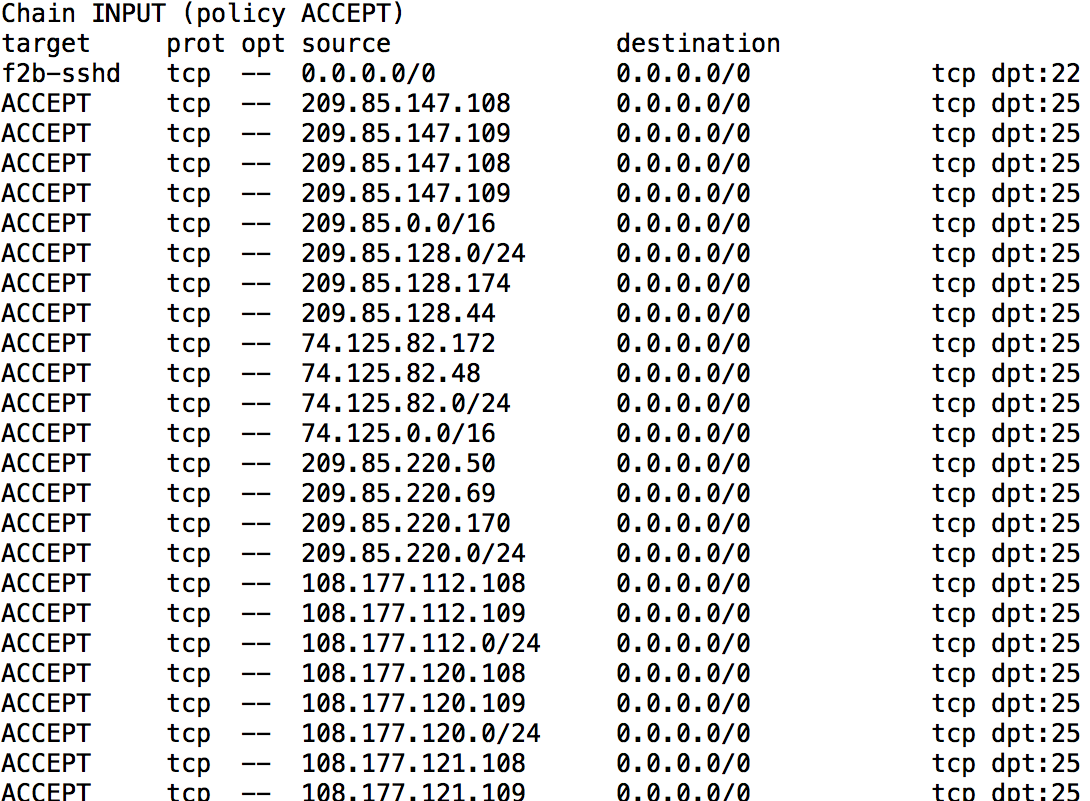
Converting a fairly elaborate iptables based firewall with proprietary anti-spam scripts to the modern firewall-command architecture without revealing any IP.
First lets take a look where we started:
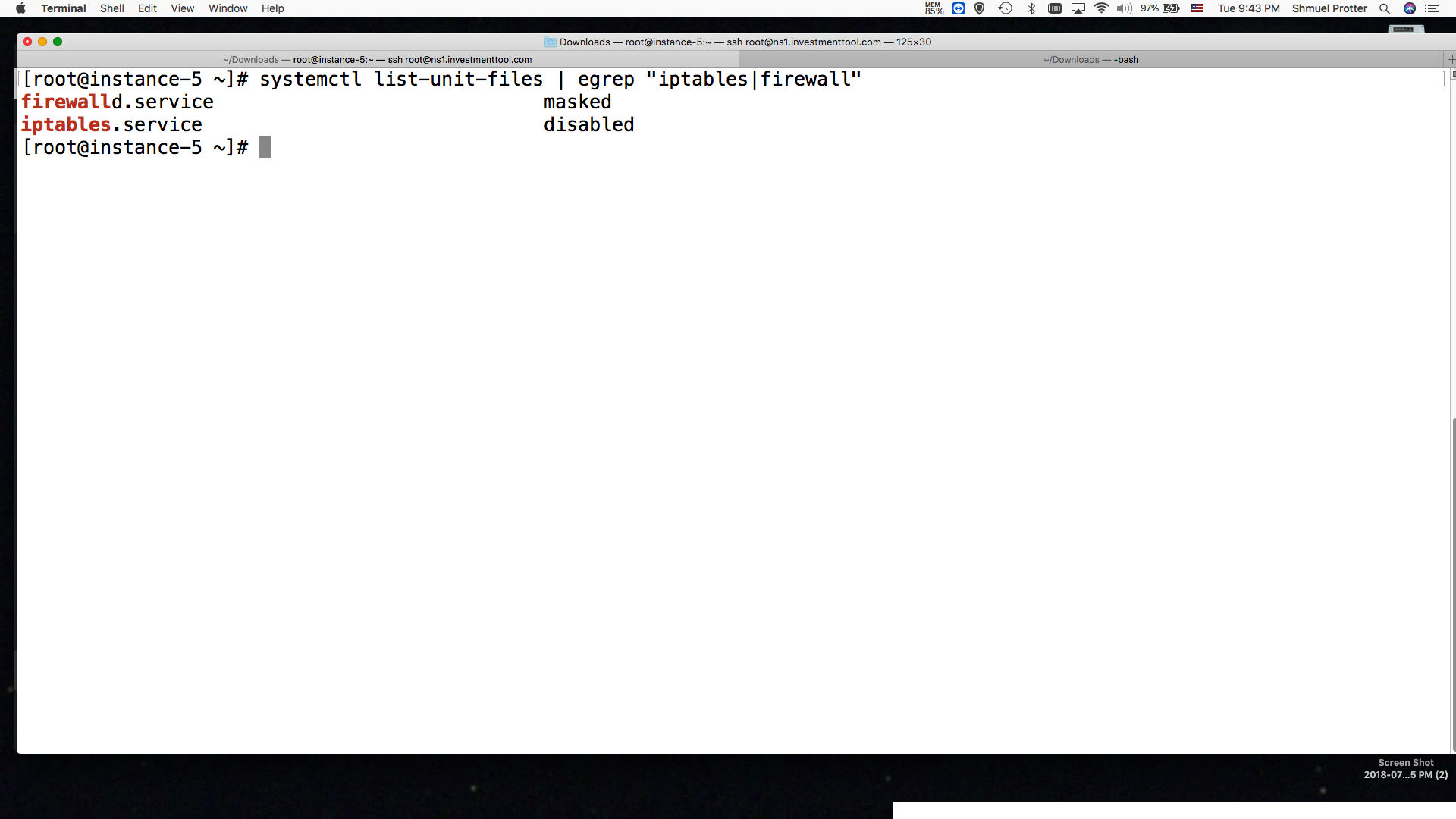
[root@instance-5 ~]# systemctl list-unit-files | egrep “iptables|firewall”
firewalld.service masked
iptables.service disabled
This shows iptables as disabled but a lot of scripts have been adding entries none the less
Most of these firewall rules relate to blocking spam smtp/mail servers. I kind f like to screw with those foks.
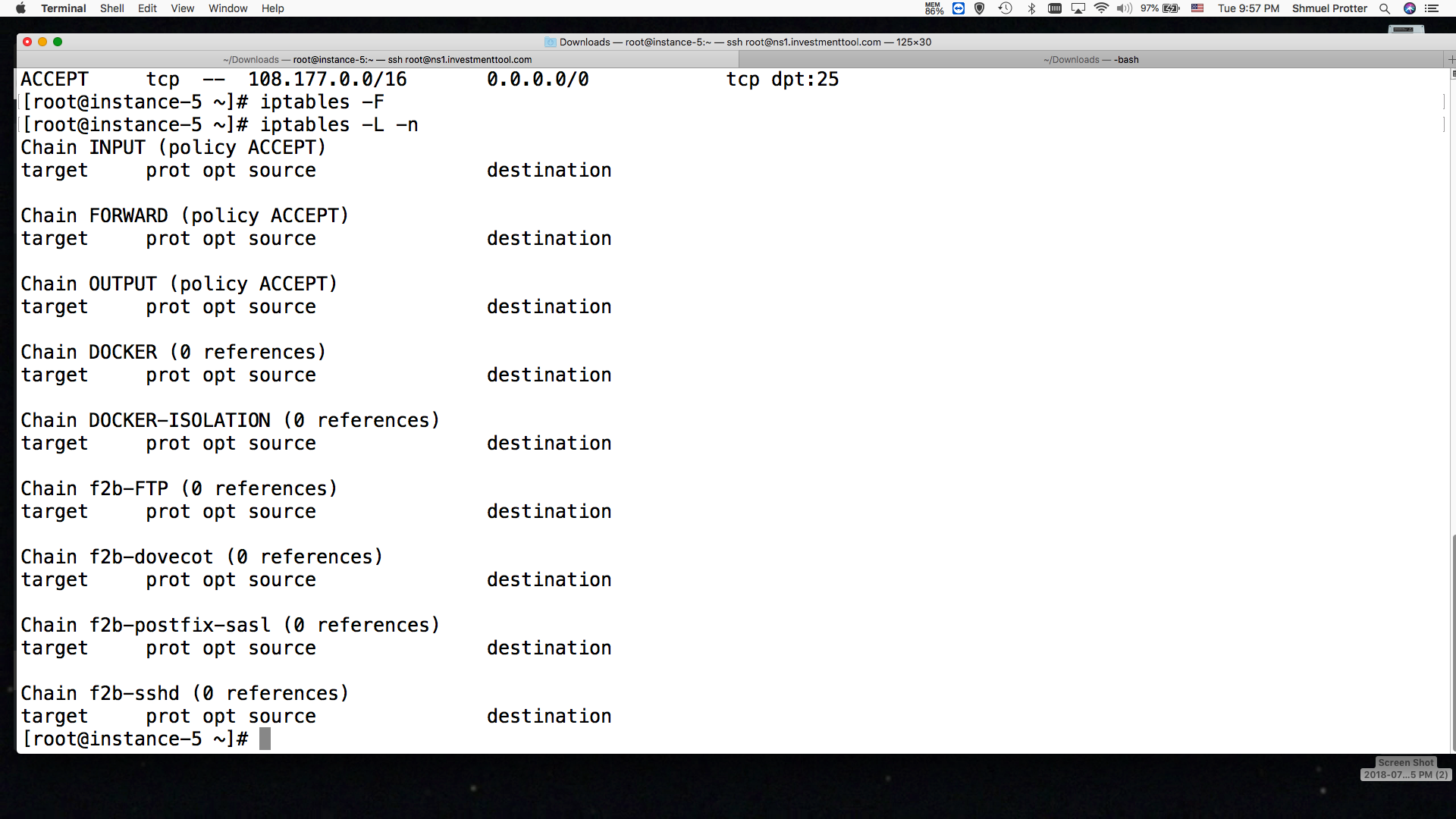
Lets clean out these entries:
iptables -F;iptables -L -n
Now we need to stop cron from running any scripts and causing trouble.
1014 systemctl disable crond
1015 systemctl stop crond
We will get a jump start with system-config-firewall
We will need to nkow which ports must remain open to service a databse cluster and the servers secondary DNS worload.
[root@instance-5 ~]# netstat -an |grep LISTEN
tcp 0 0 127.0.0.1:10026 0.0.0.0:* LISTEN
tcp 0 0 0.0.0.0:3306 0.0.0.0:* LISTEN
tcp 0 0 0.0.0.0:110 0.0.0.0:* LISTEN
tcp 0 0 127.0.0.1:783 0.0.0.0:* LISTEN
tcp 0 0 0.0.0.0:143 0.0.0.0:* LISTEN
tcp 0 0 0.0.0.0:111 0.0.0.0:* LISTEN
tcp 0 0 172.17.0.1:53 0.0.0.0:* LISTEN
tcp 0 0 10.240.0.3:53 0.0.0.0:* LISTEN
tcp 0 0 127.0.0.1:53 0.0.0.0:* LISTEN
tcp 0 0 0.0.0.0:21 0.0.0.0:* LISTEN
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN
tcp 0 0 0.0.0.0:4567 0.0.0.0:* LISTEN
tcp 0 0 127.0.0.1:953 0.0.0.0:* LISTEN
tcp 0 0 0.0.0.0:25 0.0.0.0:* LISTEN
tcp 0 0 0.0.0.0:993 0.0.0.0:* LISTEN
tcp 0 0 0.0.0.0:995 0.0.0.0:* LISTEN
tcp 0 0 127.0.0.1:10024 0.0.0.0:* LISTEN
tcp 0 0 127.0.0.1:9000 0.0.0.0:* LISTEN
tcp 0 0 127.0.0.1:10025 0.0.0.0:* LISTEN
tcp6 0 0 ::1:10026 :::* LISTEN
tcp6 0 0 :::110 :::* LISTEN
tcp6 0 0 ::1:783 :::* LISTEN
tcp6 0 0 :::143 :::* LISTEN
tcp6 0 0 :::111 :::* LISTEN
tcp6 0 0 :::8080 :::* LISTEN
tcp6 0 0 :::80 :::* LISTEN
tcp6 0 0 :::8081 :::* LISTEN
tcp6 0 0 :::53 :::* LISTEN
tcp6 0 0 :::21 :::* LISTEN
tcp6 0 0 :::22 :::* LISTEN
tcp6 0 0 ::1:953 :::* LISTEN
tcp6 0 0 :::25 :::* LISTEN
tcp6 0 0 :::443 :::* LISTEN
tcp6 0 0 :::993 :::* LISTEN
tcp6 0 0 :::995 :::* LISTEN
tcp6 0 0 ::1:10024 :::* LISTEN
[root@instance-5 ~]# systemctl start firewalld.service
Failed to start firewalld.service: Unit is masked.
[root@instance-5 ~]# systemctl unmask firewalld
Removed symlink /etc/systemd/system/firewalld.service.
[root@instance-5 ~]# systemctl enable firewalld
Created symlink from /etc/systemd/system/dbus-org.fedoraproject.FirewallD1.service to /usr/lib/systemd/system/firewalld.service.
Created symlink from /etc/systemd/system/multi-user.target.wants/firewalld.service to /usr/lib/systemd/system/firewalld.service.
[root@instance-5 ~]# systemctl start firewall
[root@instance-5 ~]# firewall-cmd –state
running
[root@instance-5 ~]# firewall-cmd –get-default-zone
trusted
[root@instance-5 ~]# firewall-cmd –get-active-zones
trusted
interfaces: eth0
[root@instance-5 ~]# firewall-cmd –get-services
RH-Satellite-6 amanda-client amanda-k5-client bacula bacula-client bitcoin bitcoin-rpc bitcoin-testnet bitcoin-testnet-rpc ceph ceph-mon cfengine condor-collector ctdb dhcp dhcpv6 dhcpv6-client dns docker-registry dropbox-lansync elasticsearch freeipa-ldap freeipa-ldaps freeipa-replication freeipa-trust ftp ganglia-client ganglia-master high-availability http https imap imaps ipp ipp-client ipsec iscsi-target kadmin kerberos kibana klogin kpasswd kshell ldap ldaps libvirt libvirt-tls managesieve mdns mosh mountd ms-wbt mssql mysql nfs nrpe ntp openvpn ovirt-imageio ovirt-storageconsole ovirt-vmconsole pmcd pmproxy pmwebapi pmwebapis pop3 pop3s postgresql privoxy proxy-dhcp ptp pulseaudio puppetmaster quassel radius rpc-bind rsh rsyncd samba samba-client sane sip sips smtp smtp-submission smtps snmp snmptrap spideroak-lansync squid ssh synergy syslog syslog-tls telnet tftp tftp-client tinc tor-socks transmission-client vdsm vnc-server wbem-https xmpp-bosh xmpp-client xmpp-local xmpp-server
[root@instance-5 ~]#
[root@instance-5 ~]# firewall-cmd –zone=trusted –add-service=https
success
[root@instance-5 ~]# firewall-cmd –zone=trusted –add-service=smtp
success
[root@instance-5 ~]# firewall-cmd –zone=trusted –add-service=dns
success
[root@instance-5 ~]# firewall-cmd –zone=trusted –add-service=wbem-https
success
[root@instance-5 ~]# firewall-cmd –zone=trusted –add-service=smtps
success
[root@instance-5 ~]# firewall-cmd –zone=trusted –add-service=smtps –permanent
success
[root@instance-5 ~]# firewall-cmd –zone=trusted –add-service=smtp –permanent
success
[root@instance-5 ~]# firewall-cmd –zone=trusted –add-service=dns –permanent
success
[root@instance-5 ~]# firewall-cmd –zone=trusted –add-service=https –permanent
success
[root@instance-5 ~]# firewall-cmd –zone=trusted –add-service=http –permanent
success
[root@instance-5 ~]# firewall-cmd –zone=trusted –permanent –list-services
smtps smtp dns https http
[root@instance-5 ~]# firewall-cmd –zone=trusted –permanent –add-port=4567/tcp
success
[root@instance-5 ~]# firewall-cmd –zone=trusted –permanent –add-port=10024/tcp
success
[root@instance-5 ~]# firewall-cmd –zone=trusted –permanent –add-port=10025/tcp
success
[root@instance-5 ~]# firewall-cmd –zone=trusted –permanent –add-port=10026/tcp
success
[root@instance-5 ~]# firewall-cmd –zone=trusted –permanent –add-port=53/tcp
success
[root@instance-5 ~]# firewall-cmd –zone=trusted –permanent –add-port=53/udp
success
[root@instance-5 ~]# firewall-cmd –zone=trusted –permanent –add-port=111/tcp
success
[root@instance-5 ~]# firewall-cmd –zone=trusted –permanent –add-port=143/tcp
success
[root@instance-5 ~]# firewall-cmd –zone=trusted –permanent –add-port=993/tcp
success
[root@instance-5 ~]# firewall-cmd –zone=trusted –permanent –list-services
smtps smtp dns https http
[root@instance-5 ~]# firewall-cmd –zone=trusted –permanent –list-ports
4567/tcp 10024/tcp 10025/tcp 10026/tcp 53/tcp 53/udp 111/tcp 143/tcp 993/tcp
This is taking the IP address list from my proprietary anti-spam software and creating firewall commands.
The command:firewall-cmd it’s not as easy to be direct with the script as is IP tables.
Yet I managed to get this code working with difficulty.
ffile is set to /tmp/fffile stands for firewall file.
/bin/cat mail.iplist | while read -r ip
do
echo “${iswlist} ${iswl} … ”
iswlist=$(/bin/grep ${ip} whitelist.ip.perm | wc -l );
iswl=$(/bin/grep ${ip} whitelist.ip | wc -l );
if [ $iswl -eq 0 ] && [ $iswlist -eq 0 ]
then
echo “ip: $(ip)”
echo firewall-cmd –permanent –zone=public –add-rich-rule=\’rule family=”ipv4″ source address=”$ip” port protocol=”tcp” port=”25″ reject\’ >> ${ffile}
fi
done
cat ${ffile} | while read -r CMD
do
echo $CMD
ksh “${CMD}”
rc=$?
echo “$rc $CMD ..”
done
firewall-cmd –complete-reload
sleep 50
firewall-cmd –zone=public –list-all